How This Digital Ledger Really Works (And Why It’s Kinda a Big Deal)
Alright, folks, gather ’round the digital campfire. You’ve heard the buzzwords – blockchain, Bitcoin, decentralization, Web3, maybe even muttered under your breath about NFTs. But what is this blockchain thing actually? How does the magic happen? Strap in, because we’re diving deep under the hood, breaking it down in plain(ish) English, US-accented style. Forget the hype; let’s talk brass tacks mechanics.
The Core Problem: The Trust Gap
First, why did we even need this? Think about how we exchange value or information online right now. Sending money? You rely on your bank (and their servers), the recipient’s bank, maybe a payment processor like Visa or PayPal. Buying a concert ticket online? You trust Ticketmaster’s database says you own Seat 14B. Voting electronically? You pray the system wasn’t hacked.
The common thread? Centralized intermediaries. We need trusted third parties to verify transactions and maintain records. This works… mostly. But it has flaws:
- Single Point of Failure: Hack the bank, corrupt the database, compromise the company – chaos ensues.
- Cost & Slowness: Middlemen take fees and add processing time.
- Opacity: You often can’t see the ledger yourself; you just trust it’s accurate.
- Vulnerability to Fraud: Centralized systems are juicy targets.
Blockchain emerged (hello, Bitcoin circa 2009!) as a radical solution: What if we could create a system where trust isn’t placed in a single entity, but baked into the system itself using math and cryptography? A system where the record is shared, transparent, incredibly hard to tamper with, and verified by a network, not a boss. That’s the promise.
The Basic Building Blocks: It’s Literally in the Name
Imagine a digital ledger – a record book. But instead of one book in a vault, countless identical copies exist on thousands of computers (called “nodes”) across the globe. This is decentralization – no single entity controls it.
Now, transactions (e.g., “Alice sends Bob 5 Bitcoin,” or “Smart Contract X releases funds to Vendor Y”) aren’t recorded one by one immediately. Instead, they’re grouped together into a “Block.”
Each block typically contains:
- Transaction Data: The specifics of the transfers or actions (sender, receiver, amount, timestamps, smart contract code execution).
- The Previous Block’s Hash: This is CRITICAL. Think of a hash as a unique digital fingerprint. It’s generated by a cryptographic hash function (like SHA-256 used in Bitcoin) – a complex math problem that takes any input data and spits out a fixed-length string of gibberish letters and numbers. Crucially:
- Unique: Even the tiniest change in the input data (changing one letter in a transaction) completely changes the output hash. Totally unpredictable.
- One-Way: You can easily generate a hash from data, but you absolutely cannot figure out the original data just from the hash.
- A Timestamp: When the block was created.
- A “Nonce” (Number Used Once): A random number miners fiddle with (more on that soon!).
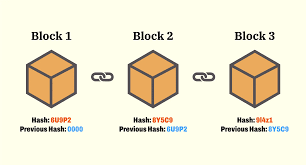
Linking the Chain: Immutability Through Cryptography
Here’s the genius part. Block #1 (the Genesis Block) has its own unique hash, calculated from its data. Block #2 includes Block #1’s hash as part of its input data. When Block #2’s data is hashed, its unique fingerprint is generated based in part on Block #1’s fingerprint.
Block #3 includes Block #2’s hash in its data, and so on.
This creates a cryptographic chain. Each block is inextricably linked to the one before it by its hash. If a sneaky bad actor tries to alter a transaction way back in Block #10:
- Changing the transaction data in Block #10 changes Block #10’s unique hash.
- But Block #11 contains the original hash of Block #10 as part of its data. Now Block #11’s stored “Previous Hash” (pointing to Block #10) doesn’t match Block #10’s new, altered hash. The link is broken!
- To “fix” this, the attacker would have to recalculate Block #10’s hash and then also change Block #11’s “Previous Hash” field to match the new Block #10 hash. But changing Block #11’s data changes Block #11’s own hash!
- Now Block #12 is broken because it contains the old Block #11 hash. So the attacker has to recalculate Block #11’s hash… which changes Block #12’s link… and so on, all the way to the latest block. They have to re-mine every single subsequent block.
This is “immutability” in action. Tampering with a historical block requires redoing all the work that came after it on the entire chain, faster than the honest network is adding new blocks. On a large, active blockchain, this becomes computationally impossible. The deeper a block is in the chain (the more blocks added after it), the more secure and immutable it becomes.
Achieving Consensus: How Does the Network Agree?
Decentralization means no central authority decides which transactions are valid or which block gets added next. So how do thousands of independent nodes scattered worldwide agree on the state of the ledger? This is solved by Consensus Mechanisms. Let’s break down the two biggest players:
- Proof-of-Work (PoW – Bitcoin, early Ethereum): Think competitive puzzle solving.
- Miners (special nodes) collect pending transactions, verify them (e.g., does Alice have enough crypto to send?), and assemble a candidate block.
- They then start furiously guessing the “Nonce” value for that block. The goal? To find a nonce such that when the entire block’s data (transactions + prev hash + timestamp + nonce) is hashed, the resulting hash meets a specific, extremely difficult target (e.g., starts with a certain number of leading zeros). This target defines the “difficulty.”
- This guessing is pure computational brute force – trillions of guesses per second. It requires massive amounts of electricity (hence the environmental concerns around Bitcoin).
- The first miner to find a valid nonce that produces a hash below the target broadcasts their solution (the “Proof of Work”) to the network.
- Other nodes easily verify the solution (hash the block data with the winning nonce – does it hit the target?).
- If valid, the network accepts this block, adds it to their copy of the chain, and the winning miner gets a block reward (newly minted crypto) + transaction fees. Everyone resets and starts mining on top of this new block.
- Why it works for consensus: Faking a block or altering history requires redoing the PoW for the altered block and all blocks after it. Because the honest network is constantly building forward with immense collective computing power, catching up and overtaking them is prohibitively expensive and unlikely (“51% attack” is the theoretical risk, but very hard on big chains). The longest valid chain (with the most accumulated work) is considered the truth.
- Proof-of-Stake (PoS – Ethereum 2.0+, Cardano, Solana): Shifting from computational power to financial stake.
- Validators (instead of miners) are chosen to propose and attest to new blocks based on how much of the blockchain’s native cryptocurrency they “stake” (lock up) as collateral.
- The selection is often random (weighted by stake size) or based on other algorithms, not a computational race.
- A chosen validator proposes a block. Other validators (“attesters”) check it. If it’s valid, they sign off (attest) on it.
- Once enough attestations are gathered, the block is finalized and added to the chain.
- Validators earn rewards for honest participation (proposing/attesting valid blocks).
- The Security Stick: If a validator acts maliciously (tries to approve invalid transactions or double-sign blocks), they get “slashed” – a portion or all of their staked crypto is burned or redistributed. Your financial skin in the game keeps you honest.
- Benefits: Vastly more energy-efficient than PoW. Faster transaction finality potential.
- Criticisms: Potential for centralization if a few entities hold massive stakes (“rich get richer”). Complexity in design.
Beyond Money: Smart Contracts & The Programmable Ledger
Blockchain’s killer app isn’t just digital cash. It’s programmability via Smart Contracts.
Think of a smart contract as a vending machine programmed into the blockchain. It’s self-executing code stored on the chain that automatically enforces the terms of an agreement when predefined conditions are met. No middleman, no ambiguity.
- Example: Simple escrow.
- Code says: “When Buyer deposits $1000 and Seller deposits the digital deed, automatically send $1000 to Seller and the deed to Buyer.”
- Once both deposits are verifiably on-chain in the correct state, the code runs exactly as written. Neither party can back out or cheat once conditions are met.
- How it Executes: When a transaction calls a smart contract function (e.g., “depositFunds()”, “releaseDeed()”), every node in the network runs the contract code locally. Because they all start from the same ledger state and run the same deterministic code, they all reach the same result. This state change (e.g., updating balances, transferring ownership of a digital asset) is recorded in the next block.
- Gas Fees: Running computation and storing data on a blockchain costs resources (nodes’ CPU, storage). “Gas” is the unit measuring this computational effort. Users pay gas fees (in the blockchain’s native crypto) to execute transactions and smart contracts. This compensates validators/miners and prevents network spam.
Deep Dive: Public vs. Private & Permissioning
- Public Blockchains (Bitcoin, Ethereum, Solana): Truly decentralized. Anyone can download the software to run a node, view the entire ledger, send transactions (if they pay gas), and (depending on the consensus) participate in mining/staking. Maximum transparency, censorship resistance, but often slower and more expensive. The “permissionless” ideal.
- Private Blockchains: Operated by a single organization or consortium. Access to run nodes, read the ledger, or write transactions is restricted to authorized participants. Faster, cheaper, more privacy for participants, but sacrifices decentralization and the “trustless” nature. Often used for supply chain tracking (Walmart, Maersk) or internal enterprise processes. More like a shared, cryptographically secured database.
- Consortium Blockchains: A middle ground. Controlled by a pre-selected group of organizations (e.g., a group of banks). Decentralized among them, but not open to the public. Balances some trust minimization among known entities with efficiency.
Real-World Applications (Beyond Crypto Speculation)
The tech is finding its footing:
- Supply Chain: Track goods from origin to shelf immutably. Prove authenticity, ethical sourcing, reduce counterfeiting (e.g., Everledger for diamonds, IBM Food Trust).
- Digital Identity: Give individuals control over verifiable credentials (diplomas, licenses) without relying on central issuers for every verification.
- Voting: Potential for highly auditable, tamper-resistant systems (though major security and anonymity challenges remain).
- Real Estate: Streamline property title transfers, reduce fraud, create transparent land registries (pilot projects globally).
- Healthcare: Securely share patient records with patient consent across providers, track pharmaceuticals.
- Intellectual Property & Royalties: NFTs for digital art/music provide proof of ownership and can automate royalty payments via smart contracts.
- Decentralized Finance (DeFi): Recreating financial services (lending, borrowing, trading, insurance) on public blockchains using smart contracts, removing traditional intermediaries.
Challenges & Criticisms: It Ain’t All Sunshine and Rainbows
Blockchain isn’t a magic bullet:
- Scalability: Public blockchains (especially PoW) struggle with transaction throughput (Bitcoin: ~7/sec, Ethereum PoW: ~15-30/sec) compared to Visa (65,000/sec). High demand = high fees & slow times. Solutions like Layer 2 (processing transactions off-chain, settling on-chain) and sharding (splitting the network) are being developed.
- Energy Consumption (PoW Specific): Bitcoin mining uses significant electricity, raising environmental concerns. PoS addresses this directly.
- Complexity & User Experience: Wallets, private keys, gas fees, seed phrases – it’s still far too complex for average users. Losing your private key means losing your assets forever. No customer support.
- Regulation: Governments are scrambling to figure out how to regulate crypto assets, DeFi, DAOs (Decentralized Autonomous Organizations), etc. Uncertainty reigns.
- Irreversibility: Immutability is a feature… until it’s a bug. If you send crypto to the wrong address or get scammed, there’s no “undo” button. No chargebacks.
- Storage & Speed: Storing the entire history of a large public blockchain requires massive storage. Achieving both decentralization, security, and speed is the “blockchain trilemma
The Future: Infrastructure, Not (Just) Speculation
The hype cycle has peaked and troughed. The real work now is building robust, scalable infrastructure and finding genuinely useful applications where blockchain’s core properties – decentralization, cryptographic security, immutability, and programmability – solve real problems better than existing systems.
Think less “get rich quick with crypto,” and more “invisible plumbing for verifiable digital interactions.” It might power the backbone of new internet architectures (Web3), enable novel forms of coordination and ownership (DAOs, NFTs with utility), or simply make specific industries more efficient and transparent.
Wrapping It Up: The Essence
So, to recap this deep dive, blockchain is fundamentally:
- A Distributed Ledger: Copies everywhere, no single owner.
- Cryptographically Secured: Hashes link blocks immutably; digital signatures prove ownership.
- Achieving Consensus: PoW or PoS (primarily) ensure network-wide agreement without a central referee.
- Programmable: Smart contracts enable automated, trustless agreements.
- Transparent (in Public Chains): All transactions are visible, auditable by anyone.
It replaces the need for blind trust in intermediaries with verifiable trust through cryptography, math, and decentralized network consensus. It’s not perfect, it’s evolving rapidly, and its ultimate impact is still being written. But understanding how it actually works – the chaining of hashed blocks, the competitive or staked consensus, the execution of code on a global computer – is crucial to seeing beyond the noise and grasping its genuine revolutionary potential. It’s a new way to build trust in a digital world. Pretty neat, huh?